Elena Canorea
Communications Lead
In the previous article about Quantum Computing, we have talked about applications of quantum computing in real life, and also we have analyzed the hardware process that is allowing the incredible speed up and also some software implications.
We will continue today with applications of quantum computing in the cybersecurity field.
We know that the sci-fi world tends to exaggerate and create a dystopian world where every new technology is feared. That’s been the case with artificial intelligence, and this is also the case with quantum computers. We’ve seen many people worry about quantum supremacy because it would mean an end to everything that is secure on the internet but let’s not jump to conclusions yet.
In cryptography, we use diverse ways to encrypt a message. Here we have two categories, the symmetric encryption with algorithms like AES, DES, IDEA, RC6, Blowfish or asymmetric encryption with algorithms like RSA, ECC, El Gamal. Another approach in cryptography is hashing, which is seen as one-way encryption. In that approach, we do not need a key to decrypt the message however the decryption of that hashed message can be achieved, but you would need some powerful computation power. This is where the threat comes from because the quantum computer promises great computational power, and there are some notable examples of quantum algorithms that can crack down on these cryptographic methods. As Akshata Shenoy, Cambou Bernard, and many others fear, there are some quantum algorithms that can break the encryptions.
For example, the RSA – protocol assumes that computers will not be able to factorize large integers in polynomial time, but when we are talking about quantum computers, that is possible with the use of Shor’s algorithm for factorization problems. Bernand supports the idea that National Security Agency should ban both ECC and RSA, both being incredibly popular in the domain.
There’s no need to panic yet…this is still a long way from reality because, as described by Ziegler Lynn, we would need “at least 10,000 qubits” or “4,000 qubits and 100 million gates” (Moses) for the Shor’s quantum algorithm on a 2048-bit RSA. And here we see that the quantum computing paradise is starting to crack, to quote Andrea Morello (Eureka Prize for Scientific Research 2011 and many more), “The greatest hurdle in using quantum objects for computing is to preserve their delicate superpositions long enough to allow us to perform useful calculations.”
In addition, hashing is thought to be secure or quantum-proof, but that is not necessarily the case because, at the end of the day, the other incredibly popular quantum algorithm is Grover’s, which is described as the best algorithm for searching in a black box (or searching in general). But this would not be as efficient as Shor’s algorithm on RSA because you still must search through all keys, so it would reduce the queries from N to √𝑁, so instead of 2256 searches, you will do 2128 searches, and it is still far from being effective.
We have talked about the threats that quantum computers bring, however, we are still far from achieving that due to hardware limitations that were explained earlier. On the other hand, we can harness the power of quantum computers today to improve cybersecurity. For example, all the encoding protocols have something in common: their need for a key. There are even some functions like HMAC that use a hashing algorithm like sha-2 combined with a key to generate a HMAC. So, keys are used everywhere, and we depend on them, but in the end, keys are just a sequence of bits. For example, RSA uses keys that are 1024, 2048, 4096 bits long, AES uses 128, 92, 256 bits long keys, and so on. But they still depend on keys that must be generated in such a fashion that they are secure. The stronger the randomness of a key, the stronger the encryption is, the stronger the randomness of each bit, and the stronger the key is. This means that the value of the bits must be generated randomly.
There are two types of random number of generators:
Of course, the second type of random number will be our approach. We can exploit the Heisenberg principle of uncertainty to guarantee the randomness of each qubit when exiting the quantum state and optimising the generation of a fixed-size-bits sequence which will be transformed into a key for an encryption protocol, but maybe we will talk more about quantum randomness in another article.
In the industry, there are more positive use cases for quantum computing like Quantum Key Distribution, Quantum coin flipping, and so on, but to understand this, let’s have a quick look at a basic theoretical quantum coin flipping algorithm that sums up to the following scenario: we have two parties (Alice and Bob) who must both agree to a random bit, but each party will try to cheat. The main objective is to ensure that both parties can agree upon one randomly generated bit without the possibility of cheating.
For this protocol, we will assume that there is a quantum channel that allows the user to send qubits that are in superposition through it. And that there is no noise that will lead to the collapse of the qubit in quantum state.
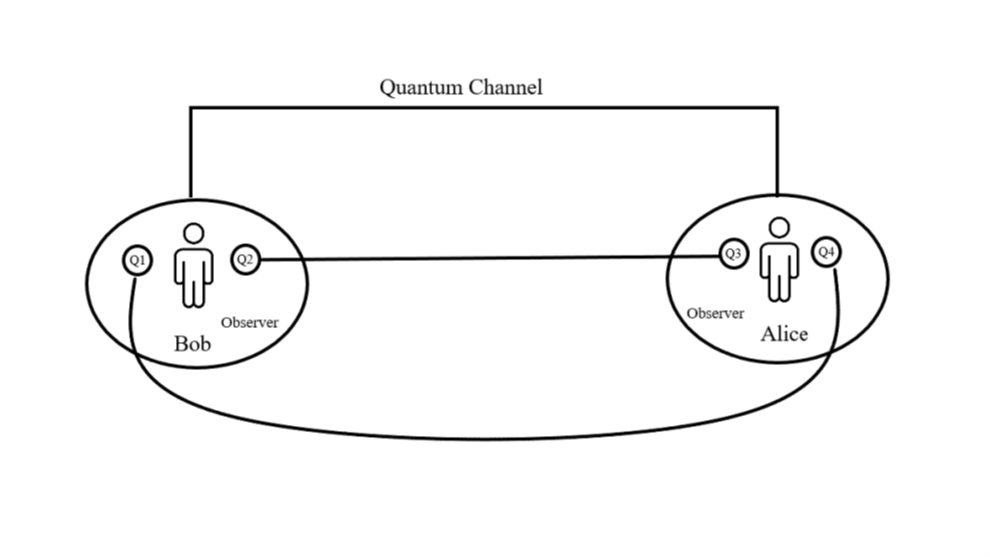
The figure above shows a small schema of how the protocol would work. To begin with, both will establish a connection through the quantum channel. Once they have established the connection, each side of the party will have two qubits and entangle them, then put them into superposition. The next step is for each party to send one of their entangled qubits to the other side through the quantum channel. Once they receive the other qubit, they can measure it.
For example, Bob had qubit Q1 and Q4 entangled and Alice Q2 and Q3, after they have sent one qubit through the quantum channel, Bob will have Q1 and Q2, and Alice will have Q3 and Q4. Now both would apply the Hadamard gate to ensure that the opposite party has not influenced the result. The next step is to measure the qubits that they received (which are in superposition). By doing so, each would obtain one random value (but because the qubit sent through the quantum channel was already entangled, measuring one would also cause the other qubit to collapse and have a binary value). At this moment, both would send the received values to the other party to test if they are identical. In this step, each party will receive the qubit value of their entangled one. If they are equal, it means that they can trust the other party, and the winning bit value would be obtained by applying the XOR logic gate to the random bits that they own. At that moment, the protocol ends with both parties having the random bit value. During this time, both parties will have an observer that would abort the protocol if the qubit received through the quantum channel is not in the superposition or if one of them would apply a gate on the opposite qubit.
To begin our protocol analysis, we will discuss the man-in-the-middle attack that would try to eavesdrop on the process. The protocol would oversee the eavesdrop attempt of a third party by abording the protocol if the qubits are not in quantum state when coming out of the quantum channel. If any of the two would send a qubit that is not entangled at the beginning of the protocol, it would fail when both parties are comparing the results therefore, the protocol is aborted. If one would try to apply gates to their qubit to influence the result, it would be in vain since the Hadamard gate would set the probability of getting 1 or 0 to 50%. In addition, the source of randomness is guaranteed by the bell’s state since each qubit is entangled with another one. In addition, the XOR logical gate is also widely used in pseudo-random algorithms, and the XOR of two guaranteed random numbers will also be a random number. This protocol is only theoretical and would provide a straightforward way for two parties to agree upon one random bit without one of them cheating.
In this series, we have discussed about the threats that quantum computing poses to the cybersecurity field but also, but we understood the challenges of making a quantum computer and how fast quantum particles become entangled, and how small the coherence length is. Therefore, one educated guess would be to rely on cloud-based quantum computing instead of hoping for a room-temperature quantum computer. By making sure that the quantum processor is hidden from any kind of waves that might interfere with the cat state of a particle, we can harness the power of quantum mechanics and try to scale.
In addition, we have the entire cloud infrastructure, and maybe in the future, the waiting queues that are currently in place for execution on a real quantum computer will be smaller, and we will be able to utilize it in the engineering world. I know that I just stated that room temperature quantum computing would never be achieved, but with the current trend in researching the time crystals discovered at Google, we might see something that will again change our perception of the world, so keep in mind: “There is no absolute truth at the quantum level” (In search of Schrodinger’s cat)
Elena Canorea
Communications Lead
| Cookie | Duration | Description |
|---|---|---|
| __cfduid | 1 year | The cookie is used by cdn services like CloudFare to identify individual clients behind a shared IP address and apply security settings on a per-client basis. It does not correspond to any user ID in the web application and does not store any personally identifiable information. |
| __cfduid | 29 days 23 hours 59 minutes | The cookie is used by cdn services like CloudFare to identify individual clients behind a shared IP address and apply security settings on a per-client basis. It does not correspond to any user ID in the web application and does not store any personally identifiable information. |
| __cfduid | 1 year | The cookie is used by cdn services like CloudFare to identify individual clients behind a shared IP address and apply security settings on a per-client basis. It does not correspond to any user ID in the web application and does not store any personally identifiable information. |
| __cfduid | 29 days 23 hours 59 minutes | The cookie is used by cdn services like CloudFare to identify individual clients behind a shared IP address and apply security settings on a per-client basis. It does not correspond to any user ID in the web application and does not store any personally identifiable information. |
| _ga | 1 year | This cookie is installed by Google Analytics. The cookie is used to calculate visitor, session, campaign data and keep track of site usage for the site's analytics report. The cookies store information anonymously and assign a randomly generated number to identify unique visitors. |
| _ga | 1 year | This cookie is installed by Google Analytics. The cookie is used to calculate visitor, session, campaign data and keep track of site usage for the site's analytics report. The cookies store information anonymously and assign a randomly generated number to identify unique visitors. |
| _ga | 1 year | This cookie is installed by Google Analytics. The cookie is used to calculate visitor, session, campaign data and keep track of site usage for the site's analytics report. The cookies store information anonymously and assign a randomly generated number to identify unique visitors. |
| _ga | 1 year | This cookie is installed by Google Analytics. The cookie is used to calculate visitor, session, campaign data and keep track of site usage for the site's analytics report. The cookies store information anonymously and assign a randomly generated number to identify unique visitors. |
| _gat_UA-326213-2 | 1 year | No description |
| _gat_UA-326213-2 | 1 year | No description |
| _gat_UA-326213-2 | 1 year | No description |
| _gat_UA-326213-2 | 1 year | No description |
| _gid | 1 year | This cookie is installed by Google Analytics. The cookie is used to store information of how visitors use a website and helps in creating an analytics report of how the wbsite is doing. The data collected including the number visitors, the source where they have come from, and the pages viisted in an anonymous form. |
| _gid | 1 year | This cookie is installed by Google Analytics. The cookie is used to store information of how visitors use a website and helps in creating an analytics report of how the wbsite is doing. The data collected including the number visitors, the source where they have come from, and the pages viisted in an anonymous form. |
| _gid | 1 year | This cookie is installed by Google Analytics. The cookie is used to store information of how visitors use a website and helps in creating an analytics report of how the wbsite is doing. The data collected including the number visitors, the source where they have come from, and the pages viisted in an anonymous form. |
| _gid | 1 year | This cookie is installed by Google Analytics. The cookie is used to store information of how visitors use a website and helps in creating an analytics report of how the wbsite is doing. The data collected including the number visitors, the source where they have come from, and the pages viisted in an anonymous form. |
| attributionCookie | session | No description |
| cookielawinfo-checkbox-analytics | 1 year | Set by the GDPR Cookie Consent plugin, this cookie is used to record the user consent for the cookies in the "Analytics" category . |
| cookielawinfo-checkbox-necessary | 1 year | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-necessary | 1 year | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-non-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Non Necessary". |
| cookielawinfo-checkbox-non-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Non Necessary". |
| cookielawinfo-checkbox-non-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Non Necessary". |
| cookielawinfo-checkbox-non-necessary | 1 year | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Non Necessary". |
| cookielawinfo-checkbox-performance | 1 year | Set by the GDPR Cookie Consent plugin, this cookie is used to store the user consent for cookies in the category "Performance". |
| cppro-ft | 1 year | No description |
| cppro-ft | 7 years 1 months 12 days 23 hours 59 minutes | No description |
| cppro-ft | 7 years 1 months 12 days 23 hours 59 minutes | No description |
| cppro-ft | 1 year | No description |
| cppro-ft-style | 1 year | No description |
| cppro-ft-style | 1 year | No description |
| cppro-ft-style | session | No description |
| cppro-ft-style | session | No description |
| cppro-ft-style-temp | 23 hours 59 minutes | No description |
| cppro-ft-style-temp | 23 hours 59 minutes | No description |
| cppro-ft-style-temp | 23 hours 59 minutes | No description |
| cppro-ft-style-temp | 1 year | No description |
| i18n | 10 years | No description available. |
| IE-jwt | 62 years 6 months 9 days 9 hours | No description |
| IE-LANG_CODE | 62 years 6 months 9 days 9 hours | No description |
| IE-set_country | 62 years 6 months 9 days 9 hours | No description |
| JSESSIONID | session | The JSESSIONID cookie is used by New Relic to store a session identifier so that New Relic can monitor session counts for an application. |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
| viewed_cookie_policy | 1 year | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
| viewed_cookie_policy | 1 year | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |
| VISITOR_INFO1_LIVE | 5 months 27 days | A cookie set by YouTube to measure bandwidth that determines whether the user gets the new or old player interface. |
| wmc | 9 years 11 months 30 days 11 hours 59 minutes | No description |
| Cookie | Duration | Description |
|---|---|---|
| __cf_bm | 30 minutes | This cookie, set by Cloudflare, is used to support Cloudflare Bot Management. |
| sp_landing | 1 day | The sp_landing is set by Spotify to implement audio content from Spotify on the website and also registers information on user interaction related to the audio content. |
| sp_t | 1 year | The sp_t cookie is set by Spotify to implement audio content from Spotify on the website and also registers information on user interaction related to the audio content. |
| Cookie | Duration | Description |
|---|---|---|
| _hjAbsoluteSessionInProgress | 1 year | No description |
| _hjAbsoluteSessionInProgress | 1 year | No description |
| _hjAbsoluteSessionInProgress | 1 year | No description |
| _hjAbsoluteSessionInProgress | 1 year | No description |
| _hjFirstSeen | 29 minutes | No description |
| _hjFirstSeen | 29 minutes | No description |
| _hjFirstSeen | 29 minutes | No description |
| _hjFirstSeen | 1 year | No description |
| _hjid | 11 months 29 days 23 hours 59 minutes | This cookie is set by Hotjar. This cookie is set when the customer first lands on a page with the Hotjar script. It is used to persist the random user ID, unique to that site on the browser. This ensures that behavior in subsequent visits to the same site will be attributed to the same user ID. |
| _hjid | 11 months 29 days 23 hours 59 minutes | This cookie is set by Hotjar. This cookie is set when the customer first lands on a page with the Hotjar script. It is used to persist the random user ID, unique to that site on the browser. This ensures that behavior in subsequent visits to the same site will be attributed to the same user ID. |
| _hjid | 1 year | This cookie is set by Hotjar. This cookie is set when the customer first lands on a page with the Hotjar script. It is used to persist the random user ID, unique to that site on the browser. This ensures that behavior in subsequent visits to the same site will be attributed to the same user ID. |
| _hjid | 1 year | This cookie is set by Hotjar. This cookie is set when the customer first lands on a page with the Hotjar script. It is used to persist the random user ID, unique to that site on the browser. This ensures that behavior in subsequent visits to the same site will be attributed to the same user ID. |
| _hjIncludedInPageviewSample | 1 year | No description |
| _hjIncludedInPageviewSample | 1 year | No description |
| _hjIncludedInPageviewSample | 1 year | No description |
| _hjIncludedInPageviewSample | 1 year | No description |
| _hjSession_1776154 | session | No description |
| _hjSessionUser_1776154 | session | No description |
| _hjTLDTest | 1 year | No description |
| _hjTLDTest | 1 year | No description |
| _hjTLDTest | session | No description |
| _hjTLDTest | session | No description |
| _lfa_test_cookie_stored | past | No description |
| Cookie | Duration | Description |
|---|---|---|
| loglevel | never | No description available. |
| prism_90878714 | 1 month | No description |
| redirectFacebook | 2 minutes | No description |
| YSC | session | YSC cookie is set by Youtube and is used to track the views of embedded videos on Youtube pages. |
| yt-remote-connected-devices | never | YouTube sets this cookie to store the video preferences of the user using embedded YouTube video. |
| yt-remote-device-id | never | YouTube sets this cookie to store the video preferences of the user using embedded YouTube video. |
| yt.innertube::nextId | never | This cookie, set by YouTube, registers a unique ID to store data on what videos from YouTube the user has seen. |
| yt.innertube::requests | never | This cookie, set by YouTube, registers a unique ID to store data on what videos from YouTube the user has seen. |
